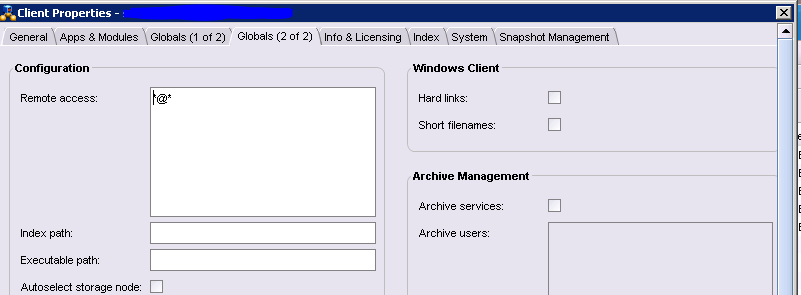
If you didn’t care when you installed EMC networker software, some consultants enter an option *@* for every client, this means that every networker client on the your network can restore data from any other clients. So, anybody can restore data of your important servers, then they can lookup and/or copy your important datas.
You can check and change this option on “EMC Networker Administration –> Configuration –> Clients” then double click on client(or right click and select Modify Client Properties) and select Globals(2 of 2)
remote access (read/write, string list)
This attribute controls who may back up, browse, and recover a
client's files. By default this attribute is an empty list,
signifying that only users on the client are allowed to back up,
browse, and recover its files. Additional users, hosts, and
netgroups may be granted permission to access this client's
files by adding their names to this attribute. Netgroup names
must be preceded by an ampersand ('&'). Each line specifies a
user or a group of users, using one of these formats:
user/host@domain , group/host@domain , user@host , user@domain ,
group@host , group@domain , &netgroup (only available on plat-
forms that support netgroups) , user_attribute=value[, ...].
where user is a user name; host is a host name; group is a user
group name; domain is a domain name; user_attribute can be user,
group, host, nwinstname, nwinstancename, domain, or domaintype
(type of the domain, NIS or WINDOMAIN).
The user attributes: nwinstname and nwinstancename are used to
indicate a NetWorker instance name. The value that should be
entered for either of these attributes is the value in the
"name" field in the NSRLA resource for the machine where a
matched user is connecting from.
value can be any string delimited by white space. If the value
has space in it, then it can be quoted with double quotes. The
value may contain wild cards, "*". Entering just a user name
allows that user to administer NetWorker from any host (equiva-
lent to user@* or */user or user=user). Netgroup names are
always preceded by an "&".
The format: user_attribute=value[, ...] is more secure because
the format is not overloaded. For example, if test@test.acme.com
is entered, then any users in the test group or users named test
and that are in the domain; test.acme.com or from the host;
test.acme.com will match this entry.
Example: The entries:
remote access: mars, *@jupiter, sam@pluto, */root;
remote access: host=mars, host=jupiter, "user=sam,host=pluto",
user=root;
are equivalent.

One thought on “EMC Networker security exploit that “Remote access””