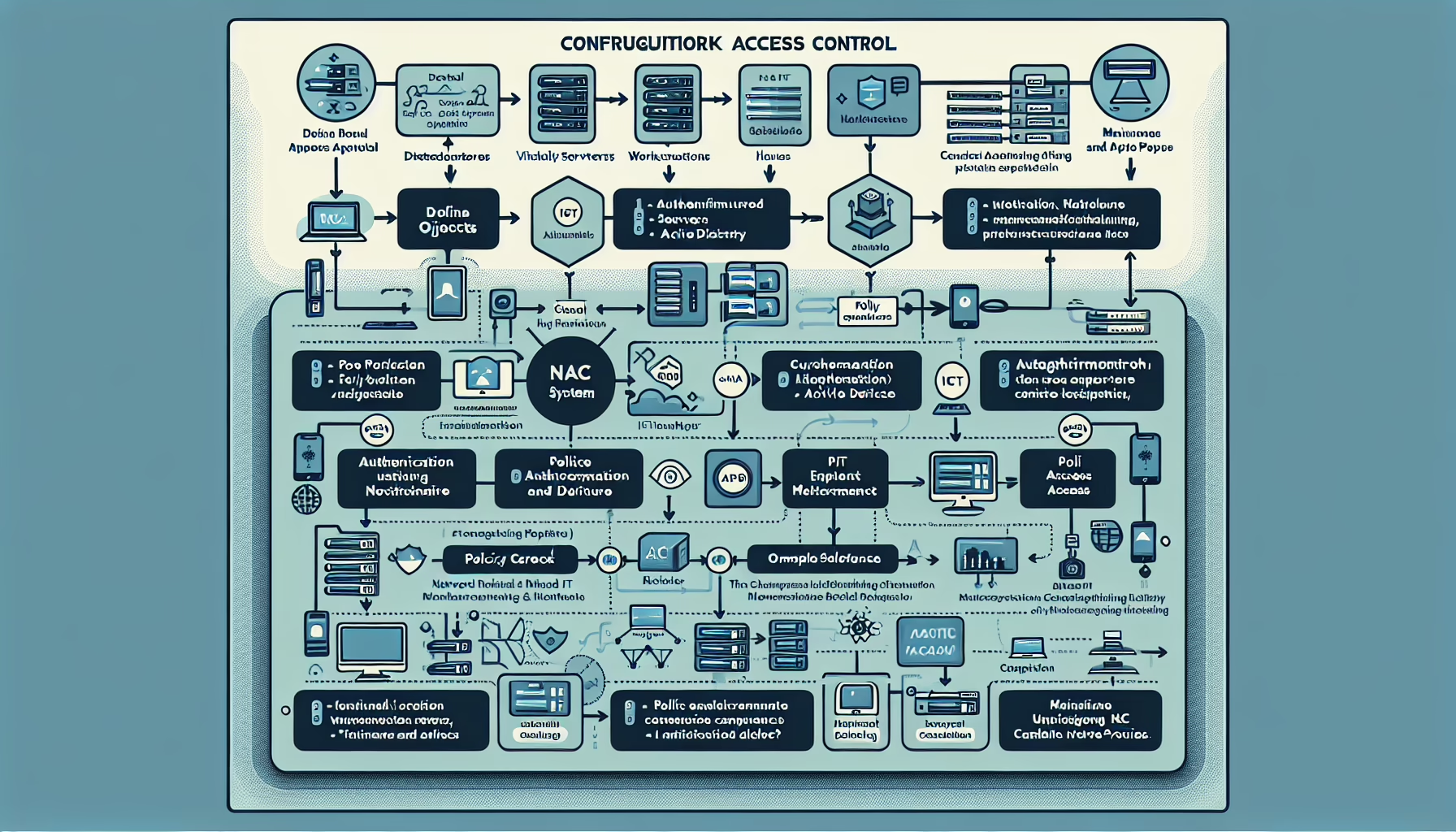
Configuring Network Access Control (NAC) is essential for securing your IT infrastructure and ensuring only authorized devices and users can access your network. NAC helps enforce security policies, prevent unauthorized access, and mitigate risks like malware infections and data breaches. Below is a step-by-step guide to configuring NAC in your IT environment:
1. Define Your NAC Objectives
- Security: Protect sensitive systems and data.
- Compliance: Meet regulatory requirements (e.g., GDPR, HIPAA).
- Visibility: Gain insight into devices and users on your network.
- Access Control: Restrict access based on roles, device type, and compliance.
2. Assess Your Network and Infrastructure
- Inventory Devices: Identify all devices (servers, workstations, IoT devices, etc.) connected to your network.
- Classify Users: Categorize users based on roles, departments, or locations.
- Evaluate Current Security Controls: Review firewalls, VLANs, authentication mechanisms, etc.
3. Choose a NAC Solution
Select a NAC platform that fits your organization’s needs, such as:
– Cisco Identity Services Engine (ISE)
– Aruba ClearPass
– Fortinet FortiNAC
– Microsoft Network Policy Server (NPS)
– Open-source solutions (e.g., PacketFence)
4. Plan Integration with IT Infrastructure
- Switches & Routers: Ensure compatibility with your network hardware. Many NAC solutions integrate with managed switches to enforce access policies.
- Authentication Servers: Integrate NAC with authentication protocols like RADIUS, LDAP, or Active Directory.
- Endpoints: Install endpoint agents (if required) on devices or configure agentless solutions.
5. Set Up Authentication Mechanisms
- 802.1X: Deploy port-based network access control using protocols like RADIUS for user/device authentication.
- Certificates: Implement certificate-based authentication (e.g., using PKI) to validate devices.
- Multi-Factor Authentication (MFA): Ensure users authenticate with additional factors beyond passwords.
6. Develop Access Policies
- User-Based Policies: Restrict access based on user roles (e.g., IT admins have full access; contractors have limited access).
- Device-Based Policies: Control access based on device types or their security posture (e.g., block unpatched devices).
- Location-Based Policies: Enforce access rules based on physical location (e.g., office vs remote).
- Time-Based Policies: Restrict access during specific hours.
7. Ensure Endpoint Compliance
- Use endpoint checks to validate compliance with security policies (e.g., antivirus, OS patches, firewalls).
- Quarantine non-compliant devices until they meet required standards.
8. Segment Your Network
- Use VLANs or micro-segmentation to isolate sensitive systems (e.g., separate production from testing environments).
- Restrict lateral movement to prevent unauthorized access between segments.
9. Implement Real-Time Monitoring
- Enable real-time monitoring of network traffic and connected devices.
- Configure alerts for unauthorized access attempts or unusual behavior.
- Use logs to audit and analyze access attempts.
10. Test and Validate NAC Configuration
- Simulate access attempts with both authorized and unauthorized devices/users.
- Test compliance checks and ensure quarantined devices can remediate issues.
- Verify seamless integration with authentication systems and network hardware.
11. Provide User Training
- Educate users on NAC policies, including authentication procedures and compliance requirements.
- Train IT staff on troubleshooting NAC-related issues.
12. Maintain and Update NAC Policies
- Review policies regularly to address emerging threats or new compliance requirements.
- Update endpoint compliance checks for new patches, antivirus versions, etc.
- Monitor and adjust access rules as organizational needs evolve.
Additional Considerations for Specific IT Areas:
For Datacenter and Servers:
- Implement NAC at the switch layer to control access to servers.
- Ensure server management interfaces (e.g., iDRAC, iLO) are accessible only from secure subnets.
For Virtualization:
- Integrate NAC with hypervisor management consoles (e.g., VMware vCenter or Hyper-V).
- Use NAC policies to restrict VM creation and migration to authorized users.
For Kubernetes:
- Leverage Kubernetes-native tools like RBAC and network policies.
- Enforce NAC for Kubernetes API access and isolate namespaces.
For AI Workloads and GPUs:
- Secure access to GPU nodes using NAC policies.
- Monitor traffic to/from AI workloads to prevent unauthorized data exfiltration.
For Remote Access:
- Enforce VPN access with NAC policies for remote users.
- Use Zero Trust principles to validate remote endpoints.
By implementing a robust NAC solution tailored to your organization’s requirements, you can significantly enhance your IT infrastructure’s security posture and ensure compliance with industry standards.