Event searching in windows security logs is too difficult, because of there are too many events in a short time.
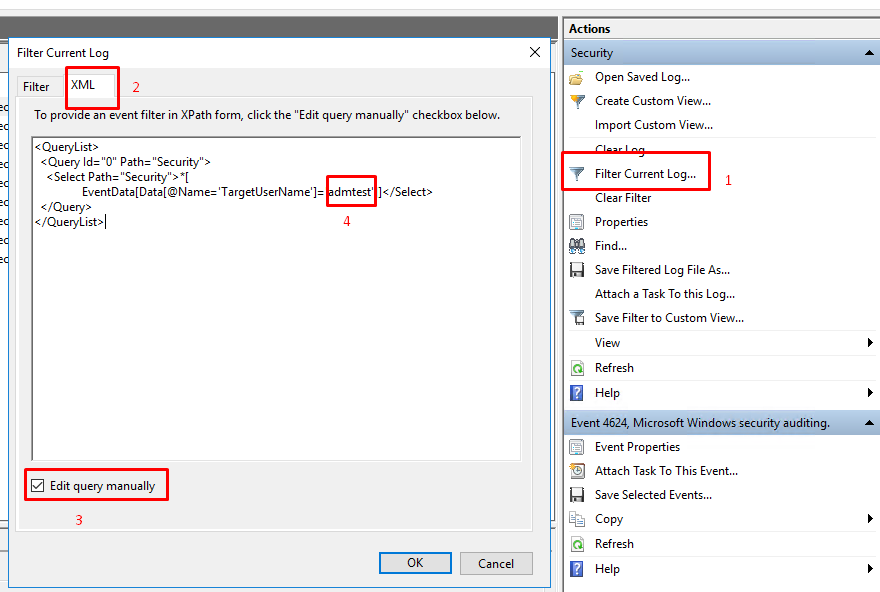
To overcome this issue we must use “Filer Current Log” in the action menu. But options in the filter windows is not enough, if you want to filter security event logs by User . (User option in Filter Window is useless for our concern)
So what can we do?
We can use XML tab of “Filter current log” window:
<QueryList> <Query Id="0" Path="Security"> <Select Path="Security">*[ EventData[Data[@Name='TargetUserName']='admtest']]</Select> </Query> </QueryList>
If you want to find user events for a spesific event id (for example “Logons”), you can use code below;
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID='4624')]
and
EventData[Data[@Name='TargetUserName']='admtest']
]
</Select>
</Query>
</QueryList>
Source: https://serverfault.com/questions/571732/filtering-security-logs-by-user-and-logon-type

Ali YAZICI is a Senior IT Infrastructure Manager with 15+ years of enterprise experience. While a recognized expert in datacenter architecture, multi-cloud environments, storage, and advanced data protection and Commvault automation , his current focus is on next-generation datacenter technologies, including NVIDIA GPU architecture, high-performance server virtualization, and implementing AI-driven tools. He shares his practical, hands-on experience and combination of his personal field notes and “Expert-Driven AI.” he use AI tools as an assistant to structure drafts, which he then heavily edit, fact-check, and infuse with my own practical experience, original screenshots , and “in-the-trenches” insights that only a human expert can provide.
If you found this content valuable, [support this ad-free work with a coffee]. Connect with him on [LinkedIn].


finally a guide that works!!!
Thanks a bunch <3
How do I add a date range? It only sends me logs for the day I run the query.