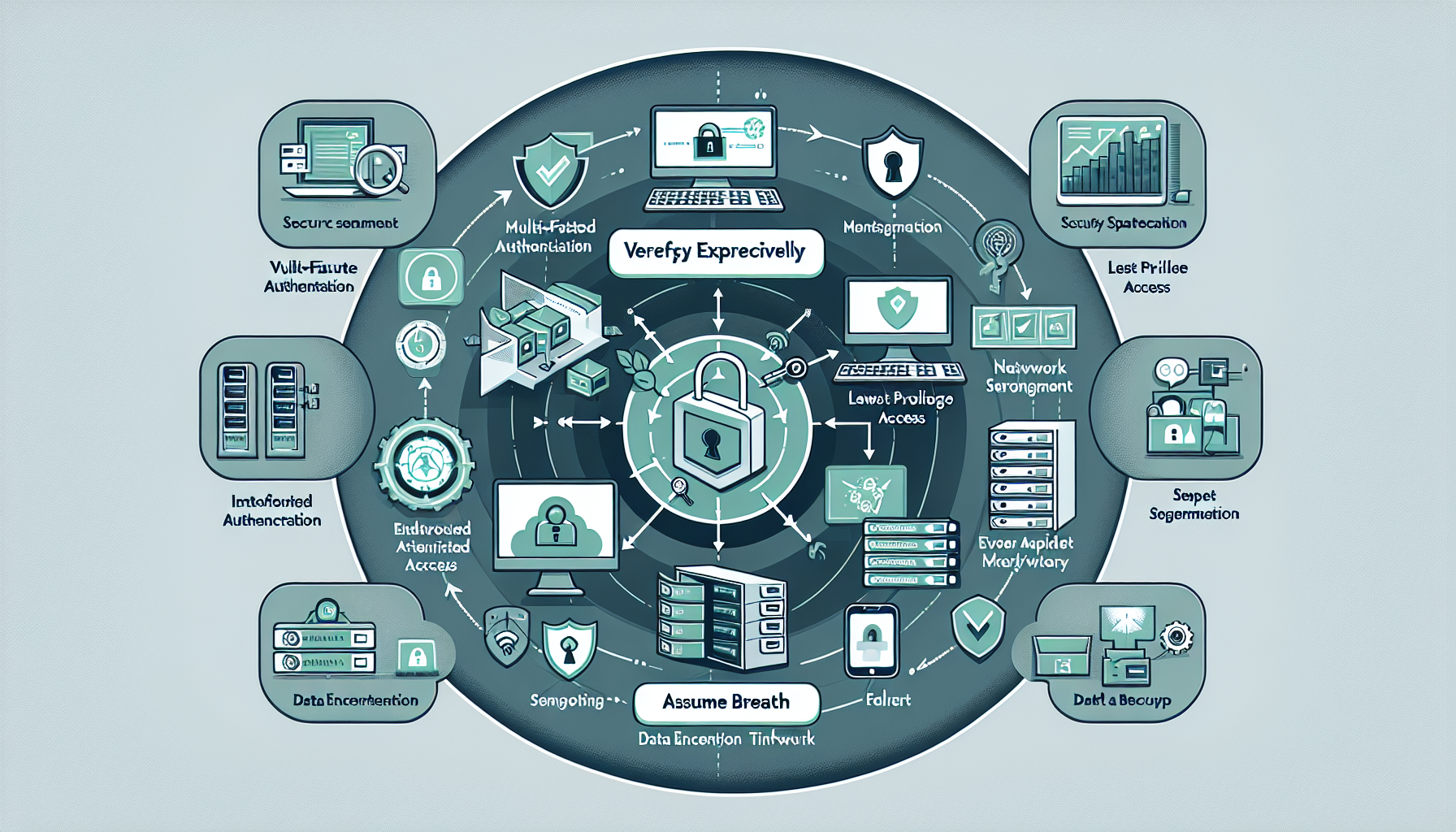
Implementing a zero-trust security model in your IT infrastructure is a critical step in ensuring robust protection against modern cybersecurity threats. Below is a step-by-step guide on how to achieve this in an environment that includes datacenters, storage, servers, virtualization, Windows, Linux, Kubernetes, and AI workloads:
1. Understand Zero-Trust Principles
Zero-trust operates on the principle that no entity—whether inside or outside the network—should be trusted by default. Key pillars of zero-trust include:
– Verify explicitly: Always authenticate and authorize based on multiple factors (identity, location, device health, etc.).
– Least privilege access: Grant the minimal level of access necessary for users and systems to perform their tasks.
– Assume breach: Design systems with the assumption that breaches have already occurred, and minimize their potential impact.
2. Conduct a Security Assessment
- Map your assets: Identify critical systems, applications, and data across your IT infrastructure, including servers, storage, virtualization platforms, Kubernetes clusters, and AI workloads.
- Assess risks: Evaluate potential vulnerabilities in your datacenter, networks, endpoints, and workloads (Windows, Linux, etc.).
- Segment your environment: Define clear zones for workloads, sensitive data, and access levels.
3. Implement Identity and Access Management (IAM)
- Centralize identity management: Use an IAM solution like Azure AD, Okta, or similar to manage user and system identities.
- Multi-factor authentication (MFA): Require MFA for all users, administrators, and service accounts. This applies to Windows/Linux systems, Kubernetes clusters, and management consoles.
- Role-based access control (RBAC): Define roles and permissions in tools like Active Directory, Kubernetes RBAC, and storage systems to enforce least-privilege access.
4. Enforce Network Micro-Segmentation
- Segment the network: Use VLANs, firewalls, and software-defined networking (SDN) to isolate workloads and limit lateral movement within your datacenter.
- Implement Kubernetes network policies: Define network policies to restrict pod-to-pod communication and enforce namespace isolation.
- Use firewalls and WAFs: Deploy perimeter and internal firewalls, as well as Web Application Firewalls (WAFs) for applications.
5. Secure Endpoints and Devices
- Endpoint protection: Deploy endpoint detection and response (EDR) solutions to secure servers (Windows/Linux), workstations, and virtual machines.
- Device compliance checks: Ensure that devices accessing your infrastructure meet security standards (patched, encrypted, etc.).
- Secure GPUs for AI workloads: For systems with GPU cards (e.g., NVIDIA), ensure drivers and firmware are up to date and apply security patches regularly.
6. Implement Strong Data Security and Backup Policies
- Data encryption: Encrypt data at rest and in transit using protocols like TLS and AES. This applies to storage systems, backups, and data flowing through Kubernetes or AI pipelines.
- Backup security: Harden backup systems by isolating them from production environments using air-gapped or immutable backups. Encrypt backup data and use strong authentication.
- Data classification: Identify sensitive data and apply stricter controls (e.g., in databases, storage arrays, and AI models).
7. Deploy Continuous Monitoring and Threat Detection
- Centralized logging: Aggregate logs from servers (Windows/Linux), Kubernetes clusters, firewalls, and storage systems into a SIEM solution (e.g., Splunk, Elastic Stack, or Azure Sentinel).
- Behavioral analytics: Use AI/ML-powered tools to detect anomalies in user behavior and network traffic.
- Endpoint monitoring: Enable monitoring for GPUs and AI workloads to detect unusual usage patterns (e.g., crypto mining or unauthorized access).
8. Protect Kubernetes and Virtualized Environments
- Kubernetes security:
- Use tools like kube-bench to evaluate compliance with security benchmarks.
- Implement secrets management using solutions like HashiCorp Vault or Kubernetes Secrets.
- Regularly scan container images for vulnerabilities using tools like Trivy or Aqua Security.
- Virtualization security:
- Harden hypervisors by disabling unused features.
- Monitor VM activity for anomalies.
- Implement VM isolation where possible.
9. Automate Security Policies
- Policy-as-code: Use tools like Terraform, Ansible, or Puppet to automate and enforce security policies across your IT infrastructure.
- Kubernetes admission controllers: Use tools like Open Policy Agent (OPA) or Kyverno to enforce security policies on Kubernetes resources.
- AI-driven automation: Leverage AI to detect and respond to security incidents in real-time.
10. Train Your Team and Foster a Security Culture
- Security awareness: Conduct regular training for your IT team and end-users on phishing, social engineering, and other threats.
- Incident response drills: Simulate security incidents to test and refine your incident response plan.
- Collaboration: Foster collaboration between development, operations, and security teams (DevSecOps).
11. Regularly Test and Improve
- Vulnerability assessments: Conduct regular penetration testing and vulnerability scans on your infrastructure.
- Patch management: Regularly update servers, storage, Kubernetes nodes, and GPU drivers to address known vulnerabilities.
- Review policies: Periodically review and update your zero-trust policies as your environment evolves.
12. Partner with Trusted Vendors
- Leverage security tools: Use enterprise-grade security solutions from trusted vendors for datacenters, endpoints, and cloud environments.
- Stay compliant: Ensure your infrastructure adheres to industry standards like ISO 27001, NIST, or GDPR.
Conclusion
Implementing zero-trust requires a mix of technical controls, process improvements, and cultural changes. Start small by focusing on high-priority areas, then expand as your team becomes more familiar with zero-trust concepts. By adopting this model across your datacenter, virtualization platforms, Kubernetes clusters, and AI workloads, you can greatly enhance your organization’s security posture and resilience.

Ali YAZICI is a Senior IT Infrastructure Manager with 15+ years of enterprise experience. While a recognized expert in datacenter architecture, multi-cloud environments, storage, and advanced data protection and Commvault automation , his current focus is on next-generation datacenter technologies, including NVIDIA GPU architecture, high-performance server virtualization, and implementing AI-driven tools. He shares his practical, hands-on experience and combination of his personal field notes and “Expert-Driven AI.” he use AI tools as an assistant to structure drafts, which he then heavily edit, fact-check, and infuse with my own practical experience, original screenshots , and “in-the-trenches” insights that only a human expert can provide.
If you found this content valuable, [support this ad-free work with a coffee]. Connect with him on [LinkedIn].