Introduction
Windows Event Logs are crucial for both security and troubleshooting within IT environments. Whether you’re managing a datacenter or overseeing the security of an enterprise network, optimizing these logs can save valuable time and enhance your overall security posture. In this article, we’ll explore best practices for managing Windows Event Logs, advanced filtering techniques, and real-world use cases that highlight the importance of an optimized log management strategy.
1. Understanding Windows Event Logs
Windows Event Logs are a comprehensive record of system, security, and application events. These logs are instrumental in diagnosing issues, monitoring performance, and ensuring security compliance. They are categorized into several types:
-
- Application Logs: Events logged by applications or programs.
- Security Logs: Events related to security, such as login attempts and resource access.
- System Logs: Events logged by Windows system components.
2. The Challenges in Managing Event Logs
-
- Managing event logs can be challenging due to:
- Log Size: Large logs can be cumbersome and difficult to navigate.
- Log Retention: Determining how long to keep logs before archiving or deleting them.
- Event Identification: Finding specific events within a sea of entries can be time-consuming.
3. Best Practices for Event Log Management
-
- To effectively manage your event logs, consider the following best practices:
- Set Appropriate Log Sizes: Configure log sizes based on your environment’s needs to avoid log overwriting or excessive storage use.
- Navigate to Event Viewer > Right-click on a log (e.g., Security) > Properties > Set the maximum log size.
- Configure Log Retention Policies: Define how long logs should be retained before they are archived or deleted.
- Use Group Policy: Computer Configuration > Administrative Templates > Windows Components > Event Log Service.
- Regular Log Reviews: Establish a routine for reviewing logs to identify and address potential issues promptly.
- Set Appropriate Log Sizes: Configure log sizes based on your environment’s needs to avoid log overwriting or excessive storage use.
4. Advanced Filtering Techniques
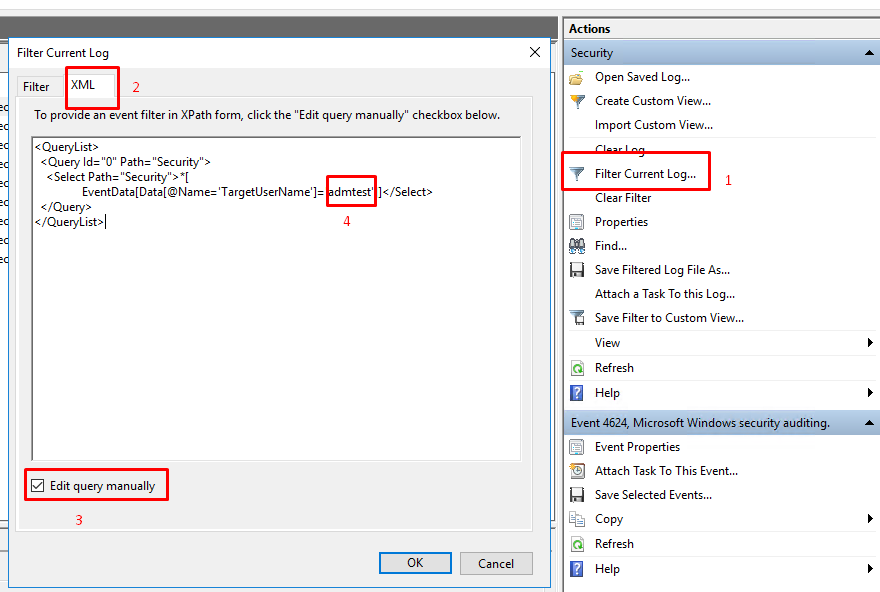
- For more precise log searches, you can use XML-based filtering. Here’s how:
- Basic User Event Filtering:
<QueryList> <Query Id="0" Path="Security"> <Select Path="Security">*[EventData[Data[@Name='TargetUserName']='USERNAME']]</Select> </Query> </QueryList>
- Filtering by Event ID and User:
<QueryList> <Query Id="0" Path="Security"> <Select Path="Security">*[System[(EventID='4624')] and EventData[Data[@Name='TargetUserName']='USERNAME']]</Select> </Query> </QueryList>
- Filtering by IP Address:
<QueryList> <Query Id="0" Path="Security"> <Select Path="Security">*[EventData[Data[@Name='IpAddress']='IP_ADDRESS']]</Select> </Query> </QueryList>
5. Automating Log Management
Automating log management can significantly enhance efficiency. Here are some tools and scripts you can use:
- PowerShell Scripts: Create scripts to archive logs periodically and clear old entries.
# Archive and clear Security log
wevtutil.exe cl Security /bu:SecurityLog.evtx
-
- Task Scheduler: Set up tasks to run scripts at regular intervals.
- Create a Basic Task in Task Scheduler and configure it to run your PowerShell script.
- Create a Basic Task in Task Scheduler and configure it to run your PowerShell script.
- Task Scheduler: Set up tasks to run scripts at regular intervals.
6. Enhancing Security with Event Logs
- Event logs can be a goldmine for identifying suspicious activities. Integrating Windows Event Logs with a Security Information and Event Management (SIEM) system can provide deeper insights and proactive threat detection.
- Suspicious Login Attempts: Monitor for multiple failed login attempts to detect potential brute-force attacks.
- Unauthorized Access: Track access to sensitive files and folders to detect unauthorized activities.
7. Real-world Use Cases
Use Case 1: Detecting Brute-force Attacks
A company noticed multiple failed login attempts in their Security logs. By filtering logs with Event ID 4625 (Failed login) and analyzing the IP addresses, they identified a potential brute-force attack and blocked the offending IP.
Use Case 2: Investigating Data Breach
An organization experienced a data breach. By filtering event logs for specific user activities and file access events, they traced the breach to a compromised user account and took corrective actions.
Conclusion
Optimizing and managing Windows Event Logs is essential for robust security and effective troubleshooting. By implementing best practices, using advanced filtering techniques, and automating log management, you can significantly improve your ability to monitor and secure your IT environment. Don’t forget to integrate these logs with a SIEM system for enhanced security insights.

Ali YAZICI is a Senior IT Infrastructure Manager with 15+ years of enterprise experience. While a recognized expert in datacenter architecture, multi-cloud environments, storage, and advanced data protection and Commvault automation , his current focus is on next-generation datacenter technologies, including NVIDIA GPU architecture, high-performance server virtualization, and implementing AI-driven tools. He shares his practical, hands-on experience and combination of his personal field notes and “Expert-Driven AI.” he use AI tools as an assistant to structure drafts, which he then heavily edit, fact-check, and infuse with my own practical experience, original screenshots , and “in-the-trenches” insights that only a human expert can provide.
If you found this content valuable, [support this ad-free work with a coffee]. Connect with him on [LinkedIn].